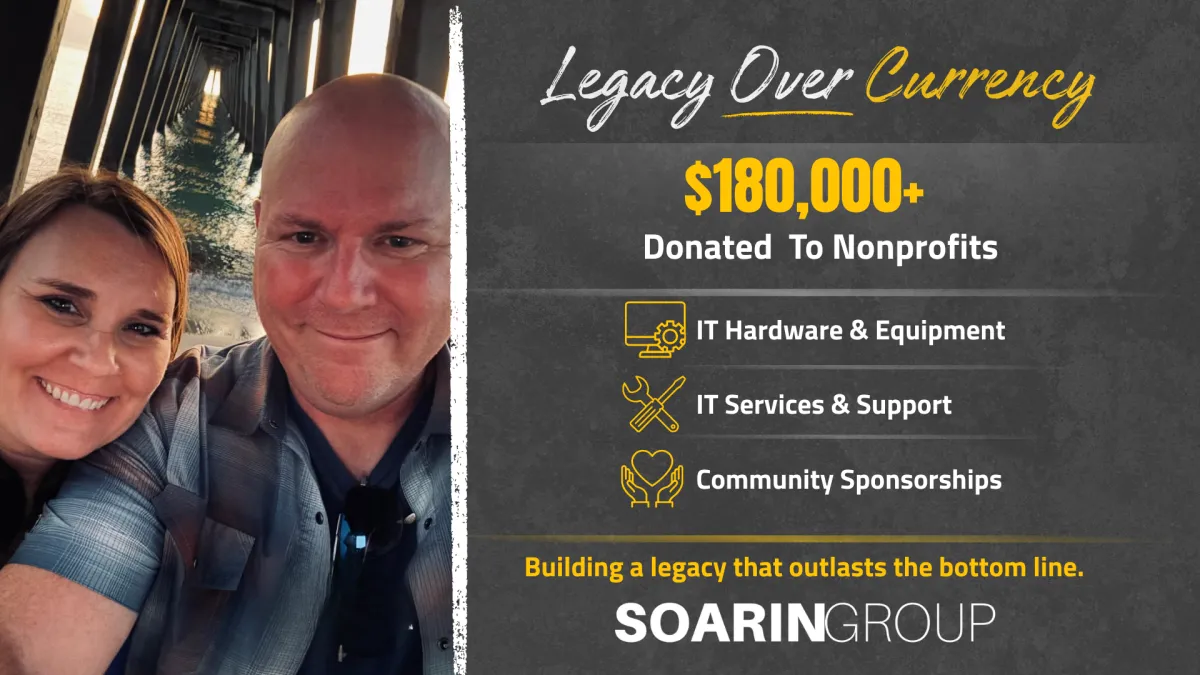
Legacy Over Currency: Building Impact Beyond Business
In Fiscal Year 2025, Soarin Group provided over $180,000 in IT hardware, services, and community sponsorships to local nonprofits. Learn how our commitment to “Legacy Over Currency” drives real impact beyond business.